 Evgeny Pro
Posted in Component Development 11 months ago
Evgeny Pro
Posted in Component Development 11 months ago
Hello,
I am trying the API and see that most of the parameters, including authentication token, are kept in URL, not Bearer token in header.
I think it's not secure as token and other parameters get logged. Just wonder what is the reason behind this solution and if there are plans to change this approach in the future?
I am following this manual
Thanks
 Evgeny Pro
Replied 9 months ago
Evgeny Pro
Replied 9 months ago
Hello again,
Just to finish the previous conversation - this is what I was trying:
This request works:
curl -X GET 'http://example.ossn/api/v1.0/user_details?guid=1&api_key_token=***' \
--header 'Content-Type: application/json'
This one not. Token is the same in both examples. Probably I misunderstand what you mean under "POST data place". Would you please advise how to amend this request?
curl -X POST 'http://example.com/api/v1.0/user_details?guid=1' \
--header 'Content-Type: application/json' \
--header 'Authorization: Bearer ***'
Thanks
 Evgeny Pro
Replied 11 months ago
Evgeny Pro
Replied 11 months ago
I see. It would be helpful to have a full request example if possible.
In most of the cases I saw, API key was a part of Authorization Bearer header and the payload in the body in JSON format. As I understand here the approach is different?
 Arsalan Shah
Replied 11 months ago
Arsalan Shah
Replied 11 months ago
Wrong, if its POST the data must not contain in the URL arguments. URL must be only
https://yourwebsite.com/api/v1.0/user_add
Rest stuff should be in POST data place
 Evgeny Pro
Replied 11 months ago
Evgeny Pro
Replied 11 months ago
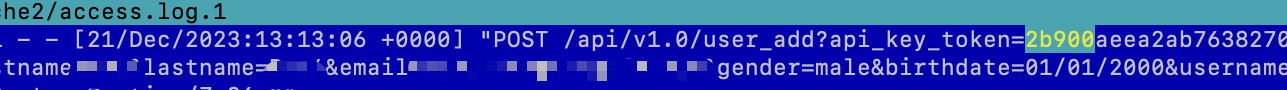
Hi!
I am sorry, I provided wrong log example. Here is the relevant one. URL parameters get logged both for POST and for GET requests.
Anyway, I just wanted to confirm that I am not doing anything incorrectly. So thank you for the explanation.
 Arsalan Shah
Replied 11 months ago
Arsalan Shah
Replied 11 months ago
Your logic is very very strange for me because if admin can access these logs that means they can access anything on the filesystem. They have straight access to the software files. Since you are logging this to external platforms that is you giving data to them.
The image you have shared is showing csrf ossn_token nothing to do with sensitivity or security here.
However if you are talking about API keys here Web Services API https://www.opensource-socialnetwork.org/webservices/view/3616/welcome-to-ossn-web-services-api-integrate-ossn-into-your-application then simply edit the component as per your need! Simply pass the token to POST request it shouldn't get logged by your server.
 Evgeny Pro
Replied 11 months ago
Evgeny Pro
Replied 11 months ago
Normal users of course cannot. But even for admins I would like to avoid that. Having this key any of them can access all users data.
Plus I usually stream logs to external platform (ELK, or similar) for admin, QA, and other operational purposes. And for that I am trying to exclude any sensitive information from the logs.
 Arsalan Shah
Replied 11 months ago
Arsalan Shah
Replied 11 months ago
and who can access these logs? can a normal user can access this?
 Evgeny Pro
Replied 11 months ago
Evgeny Pro
Replied 11 months ago
Of course SSL is being used.
I mean Apache logs 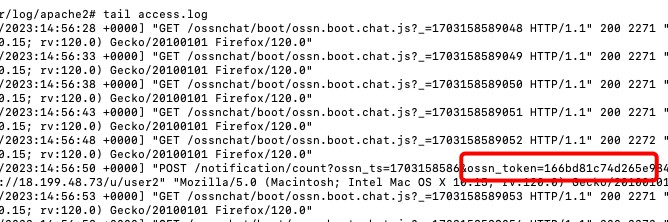 . Or maybe I am doing soemthing wrong...
. Or maybe I am doing soemthing wrong...
 Arsalan Shah
Replied 11 months ago
Arsalan Shah
Replied 11 months ago
We have no plans to change, that is why its recommended to use SSL on API calls.
Please put some more light on where its logged?
Due to the many requests in the past for additonal features and components we have decided to develope a premium version. Features like Hashtags, Videos, Polls, Events, Stories, Link Preview, etc included in it.
 $199 (Life Time)
$199 (Life Time)